Safer Communications
Encrypted and non-encrypted communication

In this part of the unit, we will briefly cover different method of communication and the different kind of encryptions. The GIF above shows that SMS is completely not encrypted, which means our Telco can see all our SMS in plaintext. This is why SMS based 2FA is not secured and discouraged.
| Unencrypted | Encrypted (but not end-to-end) | End-to-end encrypted (e2ee) |
|
|
|
In general, all chat and video applications land on one of these boxes. You should select appropriate apps to communicate with someone, depending on the nature of the conversation. For instance, if you are sharing a password with someone over SMS it can pose a security risk.
Comparing Telegram and Signal
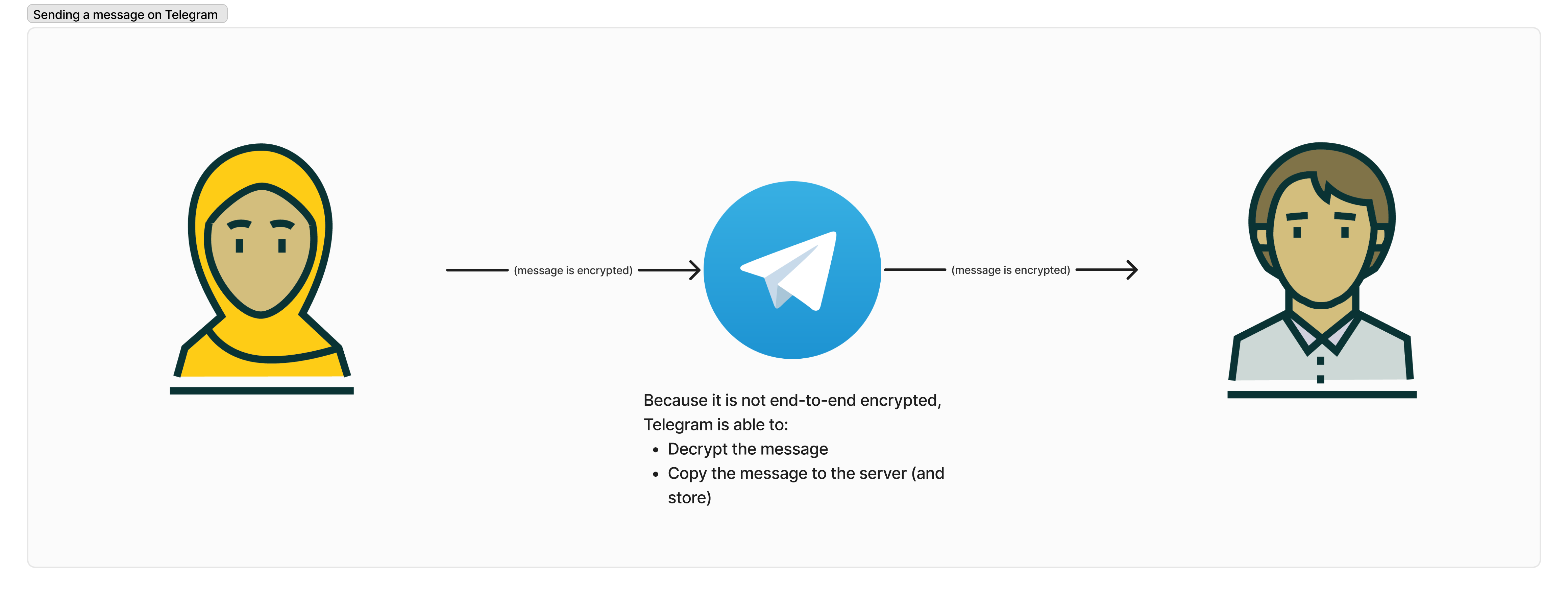
Some common messaging platform, like Instagram Chat and Telegram do not offer end-to-end encryption by default. What it means is that, the encryption is only transport layer. Which means the message is encrypted the moment it leaves your phone, but it will be decrypted at Telegram server before arriving to the receiver.
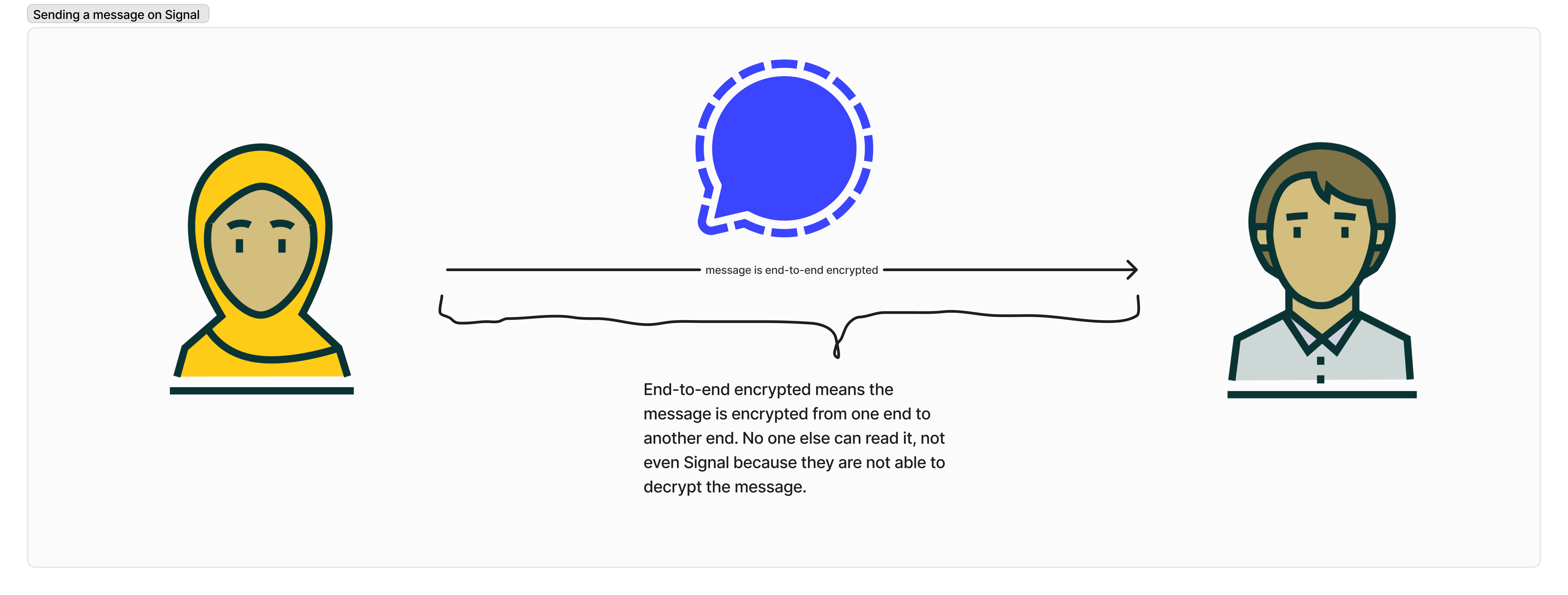
Compared to an end-to-end encrypted chat application, like Signal. The message is encrypted from one end (the sender) to the other end (the receiver). For instance, when the US government requested Signal to provide data to provide data of their users. As a company, Signal has to comply with the data request. But because it is design to collect little data, Signal is only able to provide:
- date and time a user register with Signal
- last date the user connected Signal
|
💡Bonus activity: Even though WhatsApp uses the same Signal Protocol that Signal developed, WhatsApp collects a lot more data than Signal. You can request WhatsApp to provide all the personal data that they have about you from the app itself. Once requested, you can compare how much personal data WhatsApp collected about you. Steps to request your personal data from WhatsApp: https://faq.whatsapp.com/526463418847093/ |
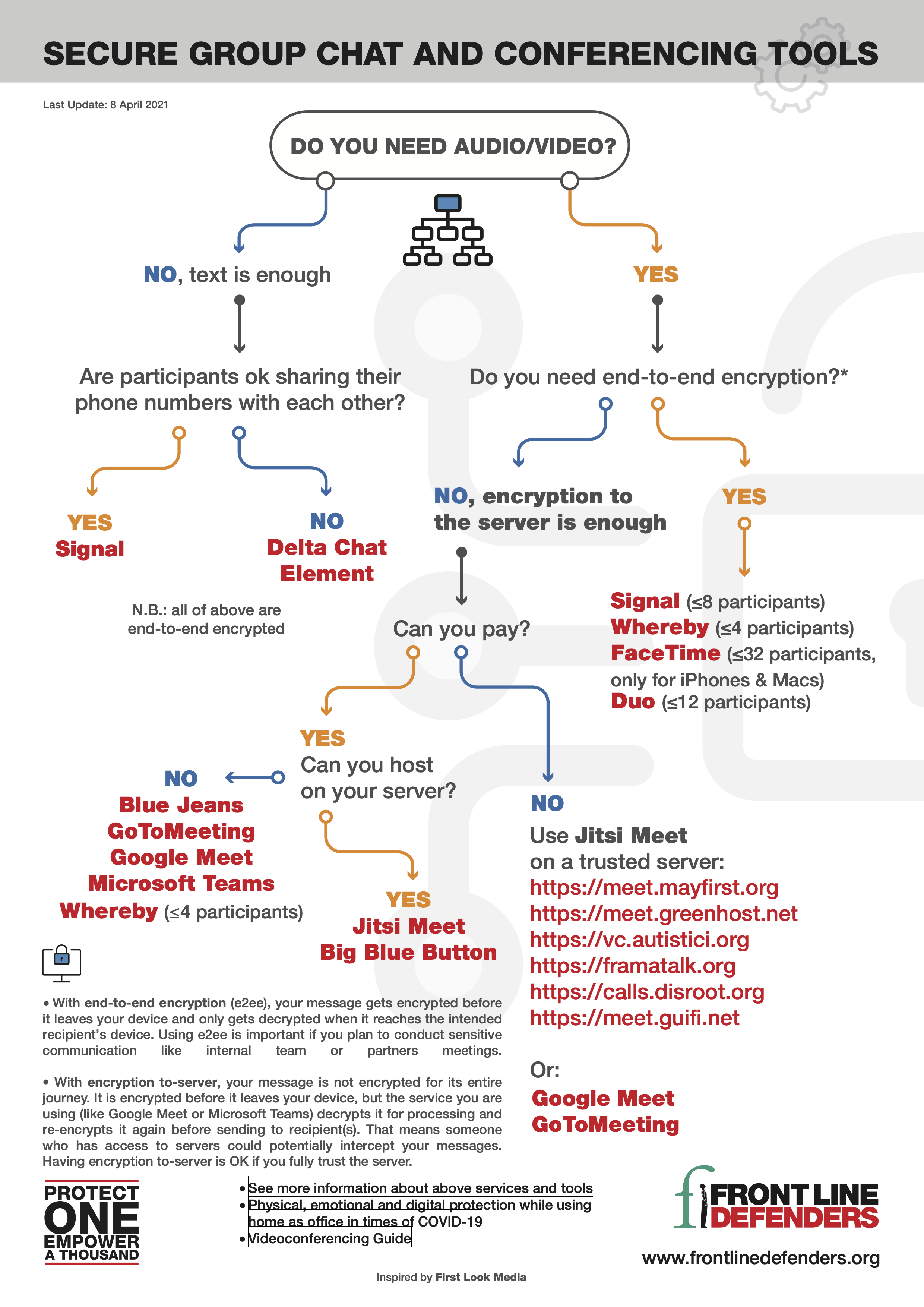
Choosing the right tool for the right purpose
This Frontline Defender Guide provides a flowchart to help us select the appropriate tool. It also provides additional criteria when choosing a platform, for instance the location of the server and how does that relate to the privacy of the tool.
Link to the guide: https://www.frontlinedefenders.org/en/resource-publication/guide-secure-group-chat-and-conferencing-tools